* refactor(web): improve 2fa enrollment process This PR will change some of the wording and colours for the 2FA processes in order to provide more clarity and address some accessibility issues for end users. The following is a summary of the changes: * One-Time Password ⭢ Time-based One-Time Password * Security Key ⭢ Security Key - U2F  * QRCode ⭢ QR Code  * `Not registered yet?` text to display `Lost device?` if a user has already registered a device of said type  * Change button and text colour in e-mails that Authelia generates * Change Authelia email footer to be more security conscious  The docs have also been updated to clarify the 2fa device enrollment limitation which only allows users to register one of each device type concurrently. Closes #1560.
2.0 KiB
| layout | title | nav_order | parent | grand_parent |
|---|---|---|---|---|
| default | Security Keys | 2 | Second Factor | Features |
Security Keys
Authelia supports hardware-based second factors leveraging security keys like Yubikeys.
Security keys are among the most secure second factor. This method is already supported by many major applications and platforms like Google, Facebook, Github, some banks, and much more...

Normally, the protocol requires your security key to be enrolled on each site before being able to authenticate with it. Since Authelia provides Single Sign-On, your users will need to enroll their device only once to get access to all your applications.
After having successfully passed the first factor, select Security Key method and click on Not registered yet? link. This will send you an email to verify your identity.
NOTE: This e-mail has likely been sent to the mailbox at https://mail.example.com:8080/ if you're testing Authelia.
Confirm your identity by clicking on Register and you'll be asked to touch the token of your security key to complete the enrollment.
Upon successful enrollment, you can authenticate using your security key by simply touching the token again when requested:
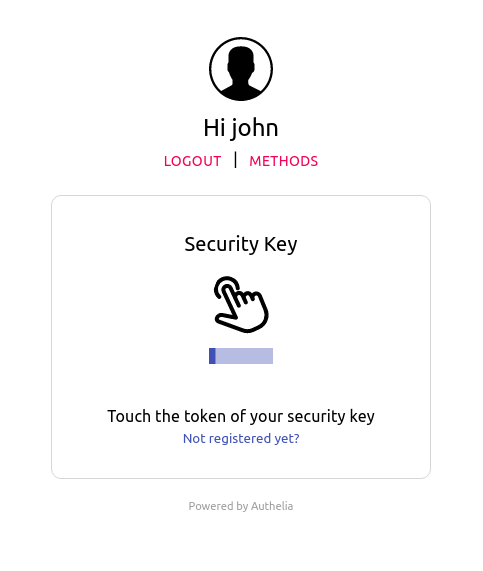
Easy, right?!
Limitations
Users currently can only enroll a single U2F device in Authelia. Multiple single type device enrollment will be available when this issue has been resolved.
FAQ
Why don't I have access to the Security Key option?
U2F protocol is a new protocol that is only supported by recent browsers and might even be enabled on some of them. Please be sure your browser supports U2F and that the feature is enabled to make the option available in Authelia.