3.1 KiB
Features in details
1-Factor (1FA) using a LDAP server
Authelia uses an LDAP server as the backend for storing credentials. When authentication is needed, the user is redirected to the login page which corresponds to the first factor. Authelia tries to bind the username and password against the configured LDAP backend.
You can find an example of the configuration of the LDAP backend in config.template.yml.
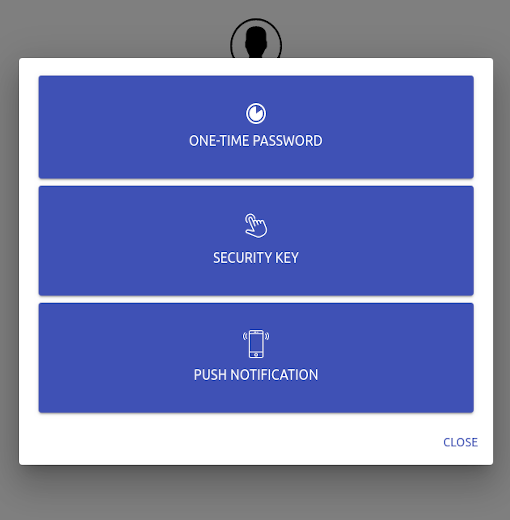
2-Factor (2FA)
Authelia comes with three kind of second factor.
- Security keys like Yubikey. More info here.
- One-Time Passwords generated by Google Authenticator. More info here.
- Duo Push Notifications to use with Duo mobile application available on Android, iOS and Windows. More info here.
Password reset
With Authelia, you can also reset your password in no time. Click on the Forgot password? link in the login page, provide the username of the user requiring a password reset and Authelia will send an email a confirmation email to the user email address.
Proceed with the password reset form and validate to reset your password.

Access Control
With Authelia, you can define your own access control rules for finely restricting user access to some resources and subdomains. Those rules are defined and fully documented in the configuration file. They can apply to users, groups or everyone.
Check out config.template.yml to see how they are defined.
Single factor authentication
Authelia allows you to customize the authentication method to use for each subdomain. The supported methods are either "single_factor" or "two_factor". Please check config.template.yml to see an example of configuration.
It is also possible to use basic authentication to access a resource protected by a single factor.
Please note that Authelia uses the Proxy-Authorization header and not Authorization since one might be willing to authenticate against both Authelia and the proxy. For instance you can use the following command to access your service:
$ curl -H "Proxy-Authorization: Basic am9objpwYXNzd29yZA==" https://myservice.example.com"
Session management with Redis
When your users authenticate against Authelia, sessions are stored in a Redis key/value store. You can specify your own Redis instance in config.template.yml.